Recent searches
Search options
Oooooooof
> Malicious code was discovered in the upstream tarballs of xz, starting with version 5.6.0. The tarballs included extra .m4 files, which contained instructions for building with automake that did not exist in the repository.
Fear not, xz users, a new developer has stepped up to take over the project:
Tia Jan <jant1203@proton.me>
The backlash thread on GitHub is already well underway: https://github.com/tukaani-project/xz/issues/92
Guy has Go project that wraps xz to provide native Go bindings. Project has had no commits for THREE YEARS.
Suddenly some guy sends a PR to update the version of xz in use to the backdoored version:
https://github.com/jamespfennell/xz/pull/2
Then you got some guy in the HN comments astroturfing everyone claiming that he knows the guy who submitted the PR IRL and he's a "cool dude", or something.
All this shit is so sus.
CAN THE FUCKING FEDS PLEASE STOP BACKDOORING OPEN SOURCE SOFTWARE PLEASE? K THANKS
oh yeah, and the guy who submitted the PR supposedly works at 1Password.
So that's nice.
Both of the maintainer accounts for the xz (under the https://github.com/tukaani-project) have been suspended, presumably by Github staff:
The suspension isn't listed on the account profile, but visible in the Following/Followers list for some reason, ex: https://github.com/JiaT75?tab=following
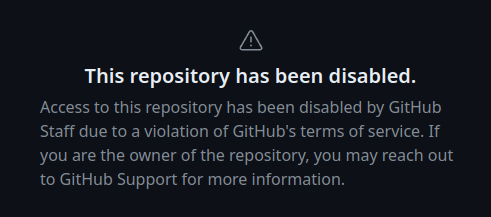
The xz project on GitHub is now disabled. Hopefully everyone who wanted the repo and full commit history already grabbed it.
Unless GitHub reverts this change, it is now impossible for researchers to view the discussion from issues and pull requests in the xz repository.
I cannot think of a legitimate reason for GitHub to censor this content: the two members of the organization had already had their accounts suspended by GitHub; it's not as if they could forcibly push over the content in the repo.
I'm not sure what to make of this move by GitHub/Microsoft, but it sure isn't a good look.
@eriner ugh I guess I really need to get moving with migrating off 1P. You think this guy is working for the feds or the chiners? Or was his GitHub account compromised? The guy was hired there 4 months ago according to LinkedIn. That timing is suspicious to me.
@eriner explain what this means
@John @eriner My unconsidered and off the cuff opinion:
0) from a technical standpoint, it's quite severe. It's exactly where you don't want this to happen
1) this doesn't have much impact on end users, because it was discovered and corrected relatively quickly, before it was incorporated in many projects, and welded deeply into many projects which might not be actively developed and updated.
3) it also points to what one might consider sloppiness and laziness, in that projects were trusting tarballs (more or less zipfiles containing pre-built output resources which are sometimes provided as a convenience), instead of taking the trouble to actually build the output code themselves from first principles, out of the original source files from the project's repository.
@John The post you're commenting on is a bit in the weeds. At a high level, the xz compression library was intentionally subverted by one of the project maintainers and a backdoor was inserted. This impacted SSH on Debian and Fedora, two very popular linux distros.
The best high-level writeup I can find is Michael Larabel's: https://www.phoronix.com/news/XZ-CVE-2024-3094
@Derdnik @John This specific attack was at least one year in the making. In particular, this commit: https://github.com/tukaani-project/xz/commit/ee44863ae88e377a5df10db007ba9bfadde3d314
and then the disabling of ifunc in google/oss-fuzz to hide the vulnerability: https://github.com/google/oss-fuzz/pull/10667
This attack didn't happen overnight, but also suggests that, given the extensive planning and setup that precipitated this backdoor, there very well may be other intentionally introduced bugs; the simple reversion of xz to a prior version may not be sufficient.
@eriner @echoteecat I might have locked it down completely too, until it can be adequately examined to figure out what the hell happened, and how far back the shenanigans go, and who was doing what, etc.
There may be some questions of legal liability which the executives want to be addressed.
It's not like they completely destroyed it, it's still there.
I agree that it will be quite questionable if it doesn't reappear within a week or so, though.
@IceCubeSoup @eriner Sure, but why not let 4chan and internet archive also get a copy of the "crime scene".
Why does the FBI get first dibs on planting evidence... I mean investigating?
@echoteecat @IceCubeSoup it makes you wonder if they're hiding it because it might unravel some threads that tie back to a "fellow cooperative department".
As far as I know, this is unprecedented by GitHub.
@eriner @echoteecat The level of success that was achieved with this penetration might also be characterized as "unprecedented" as well.
@IceCubeSoup @eriner To me, this looks like someone beat Jan Tia with a wrench to get a laptop password, and began getting code in 30 days ago.
Since then there's been a flurry of activity (sleepers activated? other wrenches?) to try to get everybody onto >5.6.0. And then this busts open less than 30 days later. Wreaks of FBI incompetence. Should have been more subtle and backdoored for years quietly.
but I do agree that incompetence is involved here at some level. Either that, or the guy is an amateur.
there was no way that this wasn't going to be discovered at some point.
If it were the NSA at the top of their game, it would have been some sort of subtle flaw in the source code implementing the crypto.
The way this was done was like duct-taping a pipe bomb to the outside of an Amazon package, and putting all inside another Amazon box.
@eriner @IceCubeSoup Huh. Neato.
@eriner DONT DO PLATFORMS - if you want to own something
@kirby oops, sorry. Fixed.
@eriner@noauthority.social dead link, is there an archive?
@nik I edited the link (typo'd originally), maybe your server hasn't picked up the edit?
Here's the fixed link regardless: https://github.com/jamespfennell/xz/pull/2
@eriner Backdooring open source software has been a concern of mine for many years, which includes Linux kernels, Linux distributions, Firefox/Fennec/Mull, Tor, Bitcoin, and so on.